Rowhammer
What is Rowhammer?#
- Physical attack on DDR3 memory
- Allows attacker to flip memory bits without directly writing them
- Allows attacker to flip bits without even "writing" (i.e. all you need is read access)
How Does DDR3 Work?#
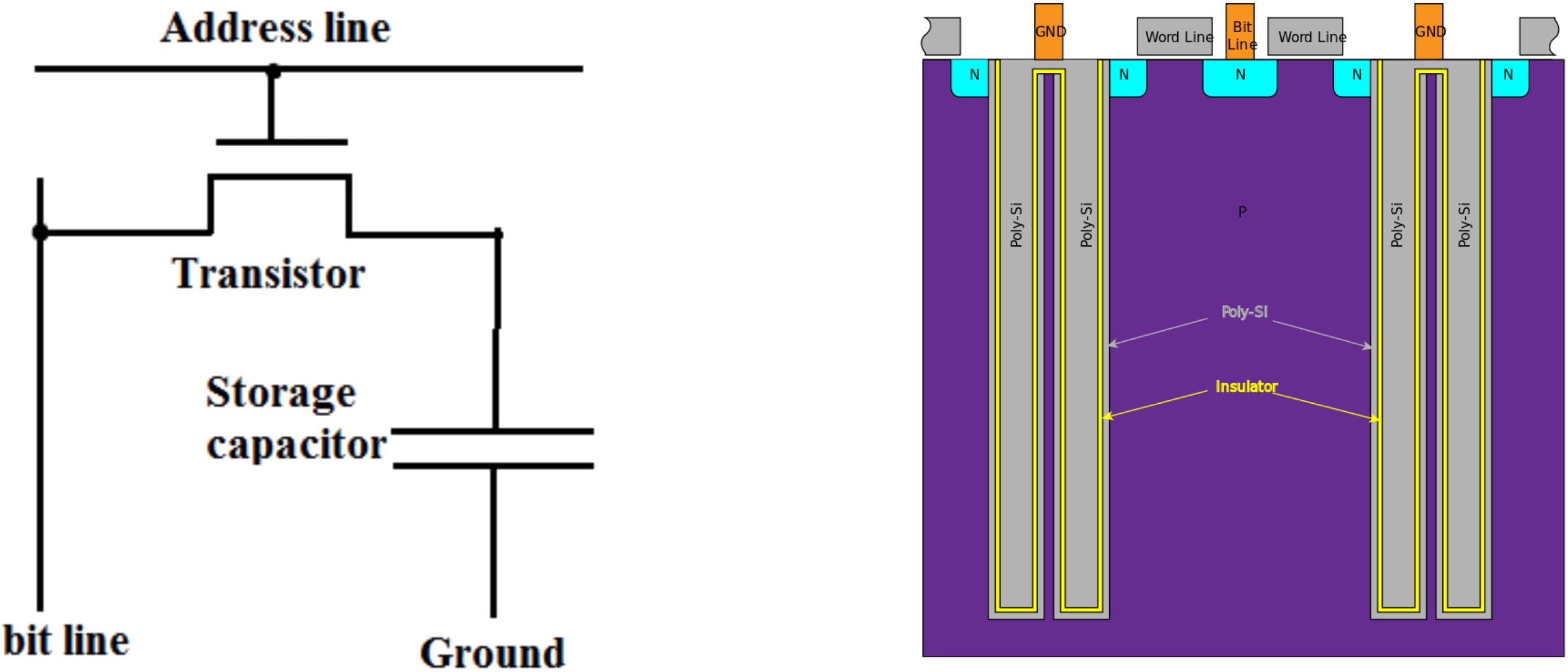
DRAM is designed to be a very compact memory architecture. The 1/0 are stored
on the storage capacitor that is left floating on the storage capacitor the
majority of the time. The capacitor is charged to write a 1 or discharged to
write a 0. Eventually, this charge leaks over a certain amount of time. With
DRAM, this needs to be refreshed. Every couple of milliseconds, the DRAM has to
be re-written by the controller otherwise zeros may start to look like ones and
visa-versa. Physically, the way this is built is using long, deep pieces of
metal (poly) that goes in the substrate to give capacitance between two plates.
To do a DDR3 write, you pre-charge the bitline to a voltage, and a bunch of cells share a bitline. Then for the cells to write to, the address lines is raised high.
Rowhammer Flaw#
- Not enough isolation between rows of DRAM
- Only started to become a major concern with DDR3, why?
- Accessing neighboring rows can flip a bit in a "victim" row
- Doesn't require write permissions to any of the rows, why?
- A read triggers a write
- Must be completed within a certain amount of time. Why?
- The DRAM controller refreshes the contents in DRAM. The attack window is between refreshes
Possible Outcomes#
- Data loss/corruption
- Program bugs
- Permission issues?
- There are many permissions on Linux that are stored in a single bit
Possible Mitigations#
- Error correcting memory
- Can generally detect and correct single bit errors, and can generally detect multi-bit errors (but can't correct them)
- Increase refresh rate
- If the refresh rate is increased, the attack window is decreased
- Memory segment isolation
- Be more careful about where privileged code is kept in memory
Rowhammer Attacks#
- Naïve attack: Wreak havoc on an unsuspecting system
- Cause processor cache to flush repeatedly
- Grab some random lines of memory and write all ones as fast as you can
- Keep writing zeros to DMA buffers
- Consequences: corrupted data, crashing programs
- Smart attack: Root a system or exfiltrate data
- Find susceptible victim bits
- Flip the victim
Rowhammer: Mitigations#
- Android update limiting app access to large chunks of contiguous memory
- Can be mitigated by ECC
Flip Feng Shui#
- Published: 2016
- Target Platform: VM with memory deduplication
- Results: Able to corrupt/modify/tweak memory in separate VM including changing public key for login access
How Flip Feng Shui Works#
- The victim VM memory puts code into the host physical memory
- The attack then boots up, and puts the same code into the host memory
- The host then sees they are the same, and points them to the same space
Rambleed Attack#
- Target Platform: Any/Ubuntu
- Results: Able to exfiltrate bits and reconstruct 2048 bit RSA key
How Rambleed Attack Works#
- Get access to parts of rows containing secret key
- Put a blank page of memory with known bit-flip vulnerabilities next to key
- Hammer secret key rows to transfer bits to your page
- Use timing attack to determine if ECC is engaging